7 Ways AI Helps SOC Teams Gather Context In Threat Investigations

TL;DR:
- AI SOC platforms like Qevlar AI go the extra mile in alert enrichment
- Qevlar AI uses context from threat intelligence sources, sandboxes and detonates files, performs visual and semantic analysis, pivots across log and telemetry sources, and applies business-specific and historical context
- On average, Qevlar autonomously runs 71 queries per investigation, work that would otherwise have to be done manually by analysts
- Result: each alert is enriched with all relevant context in under 3 minutes (on average), without swivel-chair work or human involvement
Context is what allows SOC teams to distinguish a real threat from a false positive and understand what actually matters in a specific environment.
AI SOC platforms like Qevlar AI put context at the core of incident investigations. Instead of treating alerts as isolated signals, they systematically enrich them with technical, historical, and business context, at scale.
Here are 7 concrete ways Qevlar AI can autonomously gather context for your alerts.
1. Pulls context from out-of-the-box threat intelligence sources
Threat intelligence is often the first stop in an investigation. You can connect to Qevlar with any threat intelligence platform you’re already using.
Qevlar automatically enriches observables with context from premium threat intelligence sources of your choice and out-of-the-box sources such as VirusTotal, AbuseIPDB, Urlscan, IPinfo, BigDataCloud, and other feeds. This provides immediate insight into whether an IP, domain, URL, or hash has been previously observed in malicious activity, and how recently.
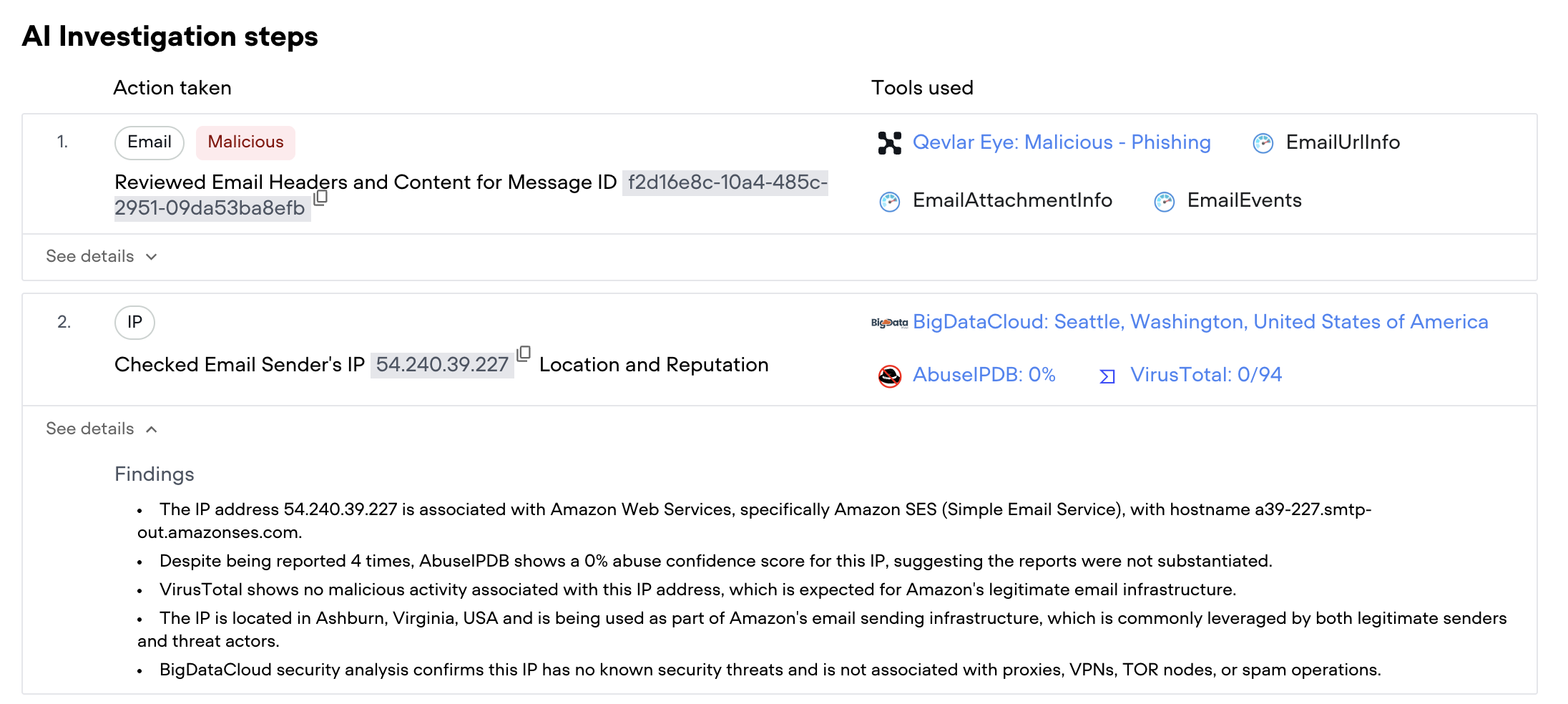
Instead of analysts manually checking multiple TI portals, this context is collected upfront and attached directly to the investigation.
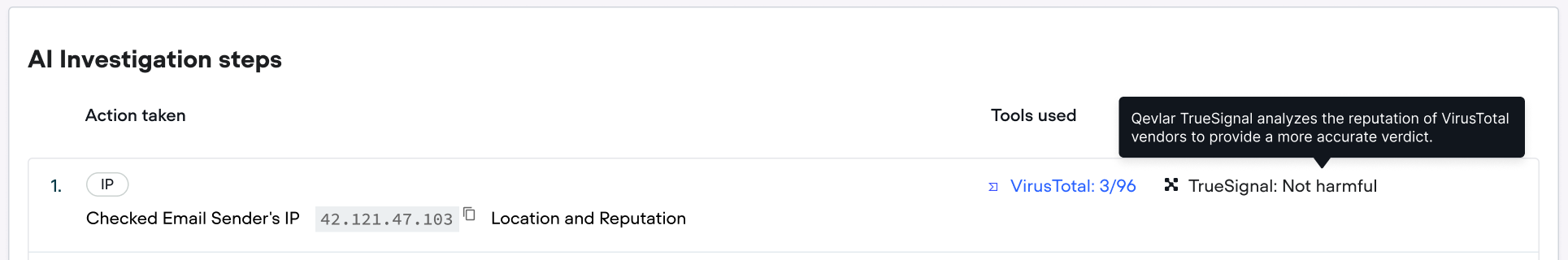
2. Filters noisy threat intel with machine learning
Qevlar applies its proprietary machine learning model, TrueSignal, to assess threat intelligence submissions, only leveraging those from reliable vendors. Instead of blindly aggregating TI results, it surfaces only high-confidence malicious indicators.
3. Downloads and sandboxes files
Qevlar automatically downloads suspicious files and detonates them in a sandbox. This adds behavioral context such as file execution, network connections, dropped artifacts, and indicators of compromis
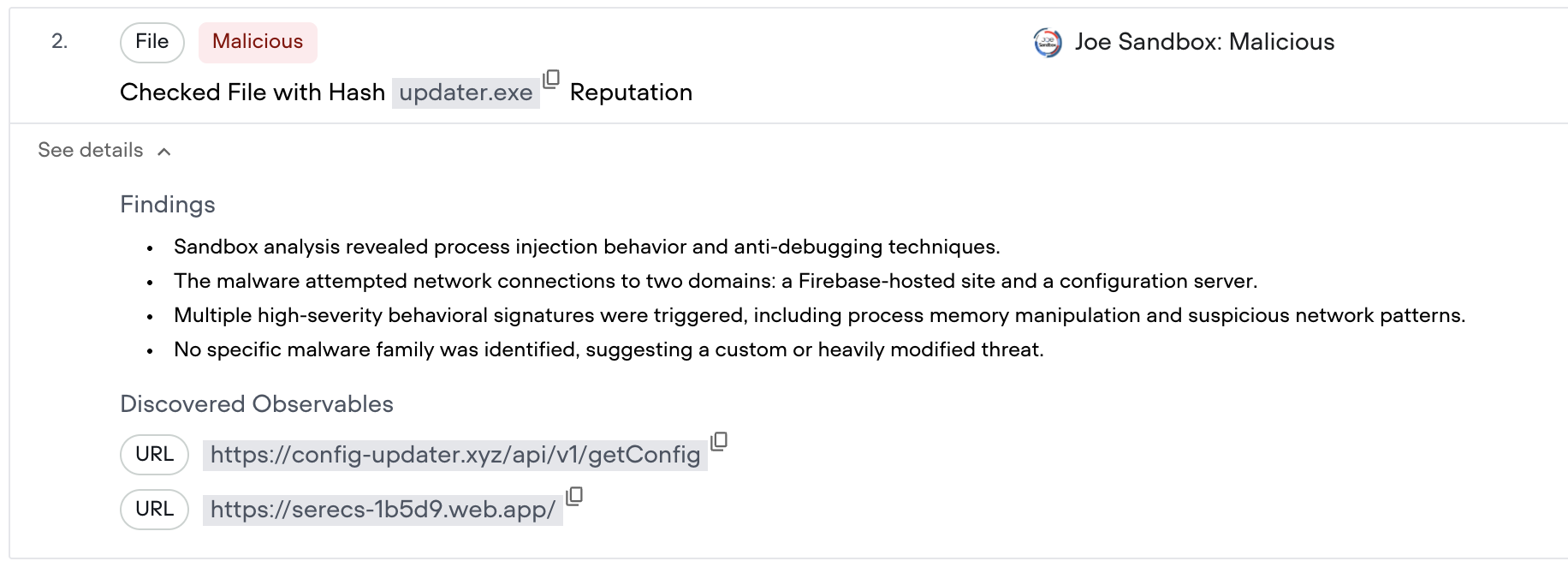
This step removes manual effort while ensuring that verdicts are based not only on static indicators, but on observed behavior.
4. Applies visual and semantic analysis to URLs and emails
Traditional detection struggles with phishing, especially when emails are visually convincing but technically benign.
Qevlar analyzes URLs and emails using its vision and semantic analysis engine, Qevlar Eye. This allows the platform to understand visual elements, language, and intent, not just headers or links.

The result is richer context around phishing attempts, including why an email is suspicious, not just that it triggered a rule.
5. Pivots across integrated tools
Qevlar pivots across integrated security tools to analyze logs and telemetry directly in the customer’s environment. This removes the need for swivel-chair investigations between SIEM, XDR, EDR, email security, and cloud platforms.
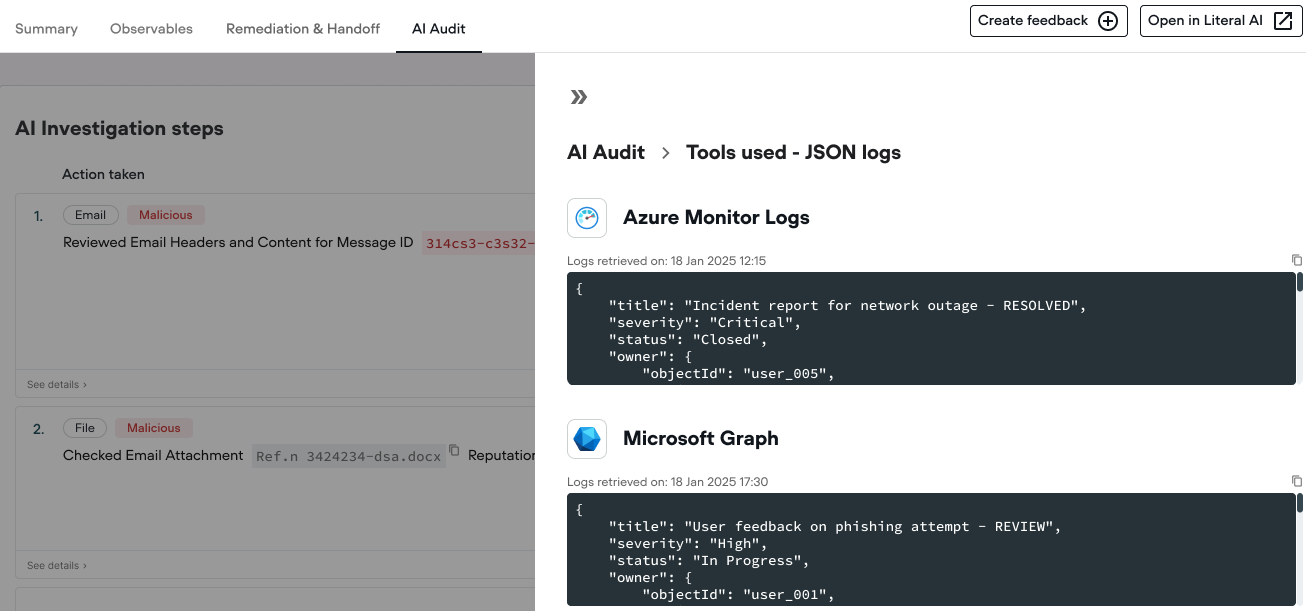
Analysts see correlated evidence in one place, with traceability back to the original data sources.
6. Applies business-specific context
What is suspicious in one environment may be completely normal in another. Memory ensures investigations reflect that reality.
Qevlar’s built-in Memory captures business-specific knowledge such as known exceptions, normal behavior, internal tools, temporary patterns, and organizational logic. This context is applied automatically during investigations.
.png)
7. Checks historical context on the same observables
Many alerts feel familiar for a reason.
Qevlar checks historical investigations involving the same observables and surfaces previous verdicts, patterns, and outcomes. This helps analysts understand whether an alert is part of a recurring issue, a known benign pattern, or an escalation.
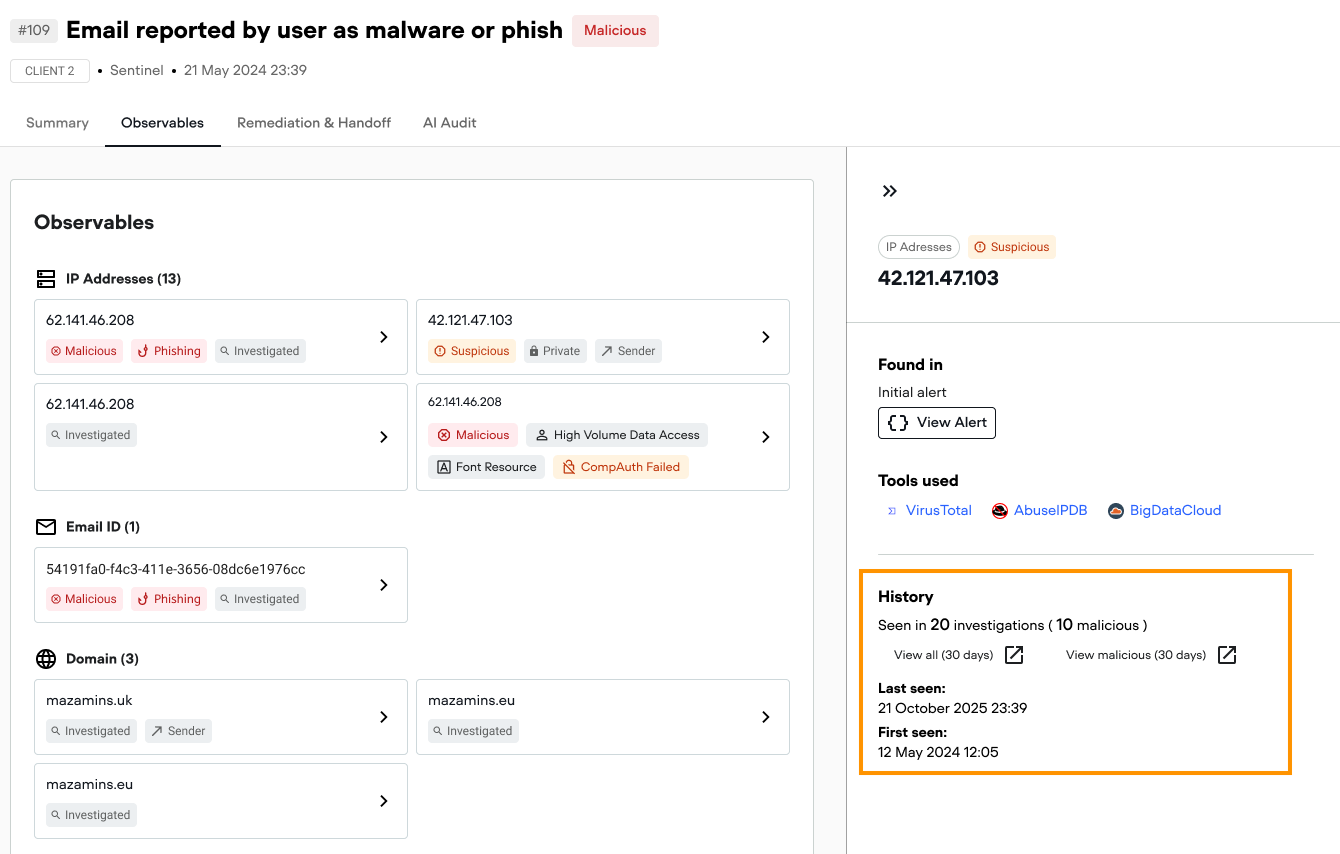
The result
Every alert is enriched with all relevant context from the start. On average, Qevlar runs 71 queries per investigation. This speaks for itself about the depth of enrichment that would otherwise require manual work.
Investigations are completed in under 3 minutes per alert on average. Highly contextualized alerts lead to high confidence in investigation outcomes, resulting in:
- Sodexo, a Fortune 500 company, cutting analyst workload by 90% on phishing investigations
- The French branch of Nomios (MSSP) scaling from 200 to over 300 customers without hiring additional analysts, while saving 50% of Level 2 analyst time
- GlobalConnect, a leading Nordic telecom provider, freeing 2,500 SOC hours within just a few months
- Orange Cyberdefence and Atos, Europe's leading MSSPs, deploying Qevlar across thousands of their customers.
Check how Qevlar investigates your alerts with same-day deployment. Book a free demo.
FAQ
How is this different from SOAR enrichment?
Traditional SOAR enrichment is rule-based and static. It follows predefined playbooks and pulls the same data in the same way, regardless of alert nuance or environment.
Qevlar’s approach is dynamic. Context is gathered based on multiple factors, including the alert type, involved observables, and available evidence. The platform reasons over multiple signals, combines technical, behavioral, historical, and business context, and adapts investigation depth accordingly.
Does this require a training or baselining period?
No long baselining period is required to get value.
Qevlar works out of the box using enrichment sources and integrated tools from day one. Business-specific context can be added gradually via built-in Memory feature, which influences investigations immediately upon approval
The system improves continuously as more investigations are completed, but meaningful results are available immediately.
How can analysts trust AI-generated context?
Trust comes from transparency.
Qevlar shows its reasoning step by step: which observables were analyzed, which tools and threat intelligence sources were used, which log queries were executed, and why a conclusion was reached. Analysts can trace every finding back to the original data source in their own environment.
This makes AI-assisted investigations verifiable, explainable, and auditable.
Can this work in MSSP environments with multiple clients?
Yes. Qevlar is built to operate at MSSP scale.
Each customer environment is fully isolated, with separate integrations, Memory, historical context, and investigation logic. Business context from one client never leaks into another.
This allows MSSPs to deliver consistent investigation quality across all customers, while still respecting client-specific behavior and requirements.
What happens when context is missing or conflicting?
Qevlar does not force a verdict when evidence is weak or contradictory.
If context is incomplete or signals conflict, the investigation reflects that uncertainty and escalates the case for human review. Conflicting threat intelligence is filtered and weighted rather than blindly aggregated.
The goal is to reduce false confidence, not hide uncertainty behind automation.






