Qevlar AI and SOAR: Different Roles, One Mission

TL;DR:
- Qevlar AI doesn’t replace your SOAR
- Qevlar AI makes your investigations more adaptive and contextual and reduces the cost of future SOAR adjustments and playbook updates.
Since SOAR platforms gained popularity in the 2020s, many SOCs have relied on playbooks to automate triage, enrichment, and response. When set up properly, they save time, but they also demand constant maintenance and can easily break.
With the rise of AI SOC Platforms, automation goes further. Platforms like Qevlar AI can autonomously adapt to changes in detection logic, or data sources and investigate alerts end-to-end on a scale. When paired with a SOAR, they create an adaptive and scalable automation layer for modern SOCs.
How Qevlar AI differs from SOARs
- Qevlar doesn’t rely on static playbooks. It enriches and investigates alerts end-to-end, adapts its path based on the available artifacts, assesses threat impact by pivoting and querying security tools, and suggests remediation actions.
- Qevlar quickly adapts to new business context, e.g. a user working from an unusual country for a specific period of time, internal network tests, using it in relevant investigations
- It works right away and doesn’t require long setup or learning time. The fastest implementation so far took just 10 minutes. It connects to security tools through an API, typically within a few hours.
Typical SOAR challenges
Even the best SOAR deployments come with well-known pain points:
- It’s time-consuming and expensive to set up a SOAR. It requires specialized expertise, which is scarce on the market. SOAR administrators are usually overloaded with requests and often have roadmaps planned a year ahead.
- Playbooks are static. Whenever you add a new data source for enrichment, you must manually update every related playbook, creating ongoing maintenance work.
- It doesn’t adapt to a changing business context. This is especially important for MSSPs, who need client-specific knowledge to be reflected in detection and response logic.
That’s where Qevlar steps in, not to replace your SOAR, but to make it more contextual and adaptive and to reduce the cost of future SOAR adjustments and playbook updates.
A Typical Setup: Qevlar on top of a SOAR
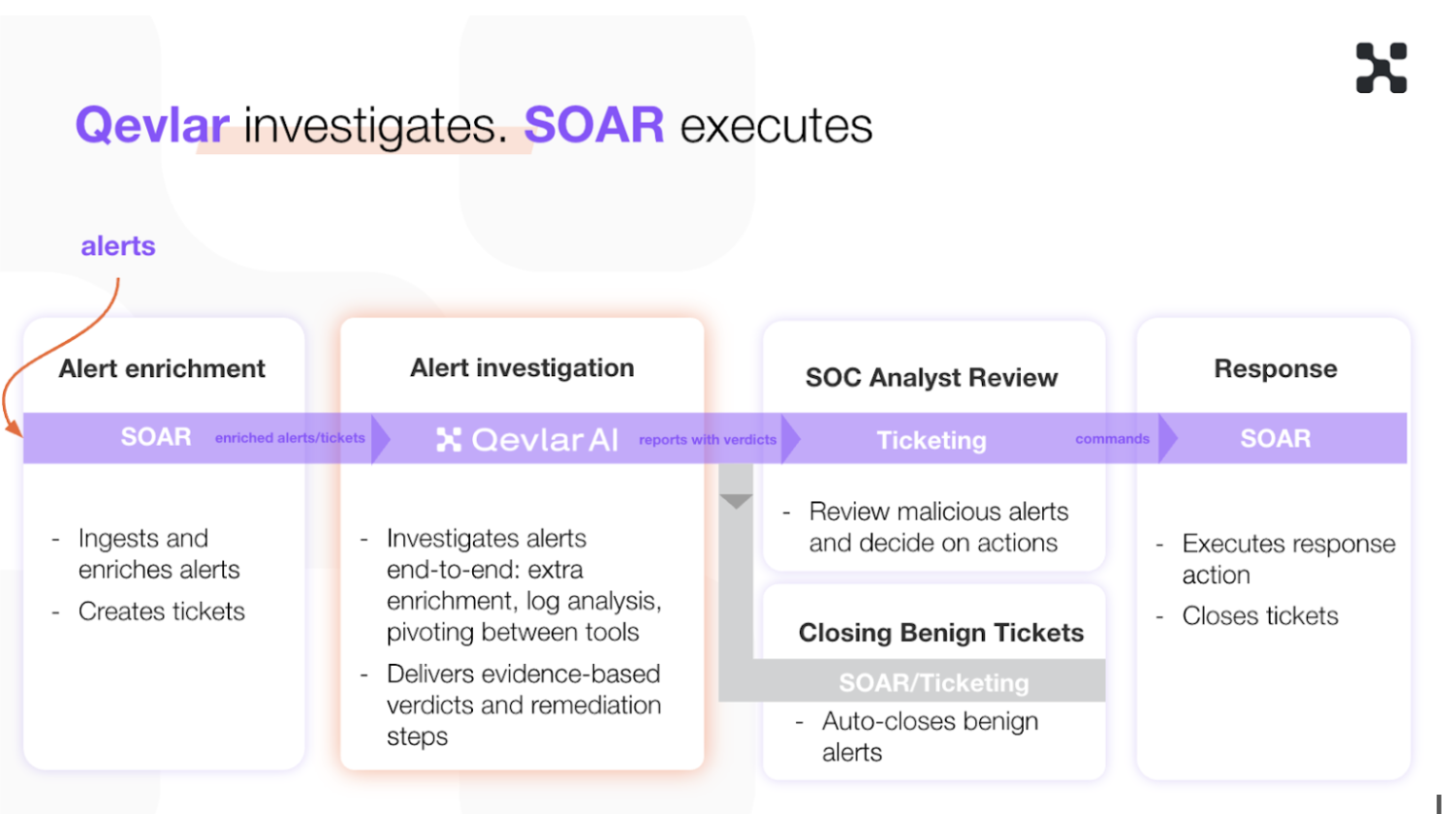
Across current Qevlar AI deployments, we usually see SOARs handling:
- Alert enrichment
- Ticket creation
- Execution of certain response actions
- Ticket closure
In such setups, Qevlar AI:
- Ingests enriched alerts directly from the SOAR.
- Adds further enrichment if new threat intel or context is available.
- Performs full investigations — querying SIEMs, pivoting between tools, and applying customer-specific context to uncover the full attack story (no need to write complex, multi-branch playbooks for your SOAR anymore!). The result is an evidence-based conclusion with a consistent logic across all cases.
- Sends verdicts back to the SOAR: typically, less than 25% of alerts are confirmed incidents. The remaining ~75% are benign and can be automatically closed.
- Feeds remediation suggestions to SOAR playbooks or ticketing systems.
- Inspires new playbooks: many customers use Qevlar’s recommendations as a foundation for building smarter response workflows.
The impact on SOCs
- 80% fewer tickets reach analysts — benign alerts are closed automatically.
- Consistent investigation quality regardless of alert source or analyst experience.
- Reduced cost and time spent on SOAR playbook updates.
Detailed comparison: SOAR, Qevlar AI, and SOAR + Qevlar AI
If you want to dive deeper into what SOCs can achieve with SOAR, Qevlar AI, and both combined, this table is for you:
.jpg)
Bottom Line
- Qevlar applies consistent investigation logic adapting the investigation path to the available artifacts and context.
- SOAR assists in enrichment and handles remediation.
- Human analysts stay in the loop and make faster, more informed decisions on the next steps.
Together, they reduce the time and cost of maintaining SOAR playbooks.
Learn how your SOC can benefit from Qevlar’s integration with your existing SOAR - Book a demo. 🔗






