The Great SOC Lie: Why We Hire Hunters and Turn Them Into Gatherers

TL;DR
- SOC hiring fails because the job analysts are promised is not the job the workflow delivers, making them quit within a year.
- The real constraint when it comes to scaling is human attention.
- Use your budget wiser: let autonomous AI handle triage, and have your analysts focus on strategic work.
- SOCs that redesign the analyst role before hiring retain talent longer and get real leverage from every new hire.
SOC Analysts’ Retention Is a Universal Problem
If you run a SOC today, the following scenario should sound familiar to you. 👇
Alert volumes continue to grow, response expectations tighten, and tolerance for mistakes shrinks. From the outside, operations may look stable, yet inside the SOC it often feels harder each quarter to stay ahead. Backlogs clear more slowly, escalation decisions feel rushed, and the team stays busy without gaining much ground.
You are not alone. In the latest survey by Splunk among 2,058 security leaders, 52% stated their SOCs are overworked.
Eventually, the discussion turns to headcount. Since the team is overloaded and incidents wait too long, hiring feels like the most direct way to absorb the pressure. After a few discussions, you get budget approval, open a role, and hope this hire will create some breathing room.
The candidates are curious, motivated, and serious about security work. They talk about wanting to investigate incidents, understand attacker behavior, and build real expertise. You describe the role in those terms because that is exactly what the SOC needs more of.
Then reality sets in.
Expectations vs Reality: What SOC Analysts Really End Up Doing Daily
When the new analyst starts, the gap between expectation and reality becomes clear within weeks.
Onboarding materials talk about investigations, threat hunting, and exposure to complex cases.
The day to day work looks very different.
Shifts begin with checking the SIEM and endpoint tools for high severity alerts, reopening closed incidents to confirm exclusions were safe, and answering internal emails asking whether an obvious phishing message is dangerous.
The rest of the time is spent closing alerts that look almost identical to yesterday’s.
Context is pulled from multiple tools. Fields are copied into tickets. Decisions are made quickly so the queue keeps moving.
On quieter days, the work is steady and repetitive. On heavier days, the backlog grows and speed takes priority over depth.
Either way, the analyst spends most of their time validating noise rather than investigating threats.
Talent and expertise get buried.
Every SOC leader recognizes this moment when the workflow delivers a very different job than the one that was promised.
Why Hiring More Analysts Won’t Help You Scale
The scale of the problem becomes obvious when the numbers are laid out.
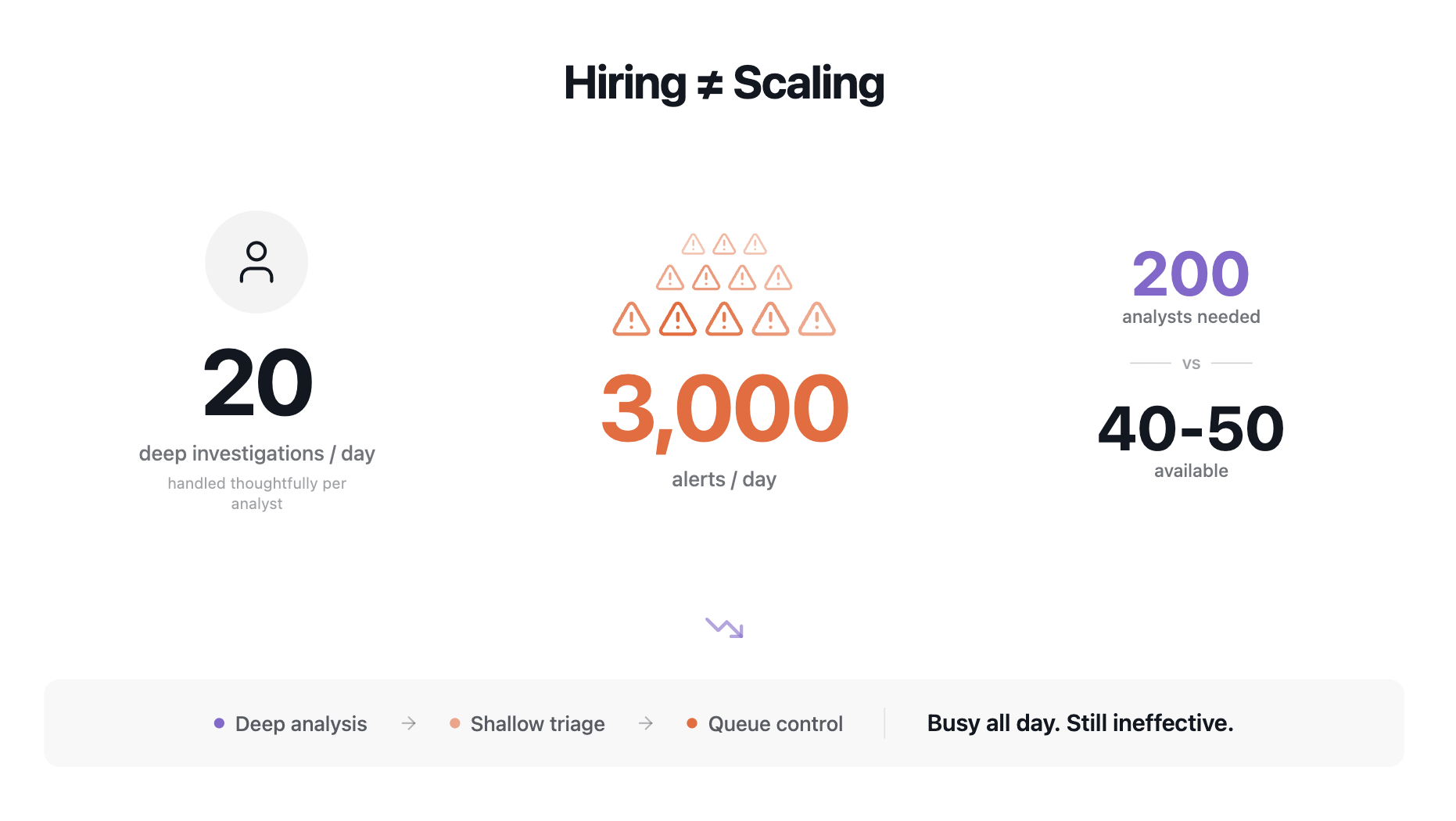
A human analyst can realistically handle around 20 deep investigations per day without cutting corners. That includes pulling context, forming a hypothesis, validating signals, and documenting conclusions.
Now look at the intake. An average SOC receives around 3,000 alerts per day. Even when most of those alerts are low quality, each one still requires a decision.
At 15 investigations per analyst per day, 3,000 alerts would require 200 analysts to handle properly. Even with more aggressive assumptions, the gap remains enormous.
Most SOCs operate with 40 to 50 people on the team (depending on the organization and its needs). Budget discussions usually allow for a couple of additional hires at a time at most.
As a result, tradeoffs become unavoidable: alerts are handled quickly, and triage becomes shallow.
The objective shifts from understanding what happened to keeping the queue under control.
Analysts stay busy all day and still feel ineffective.
There is no time or mental bandwidth for professional growth.
Industry data reflects this dynamic. 72% of cybersecurity professionals say false positives hurt productivity.
62% say false positives damage team morale more than missed alerts.
Nearly 60% say false positives take more time to resolve than real threats.
67% of organizations report a moderate to critical cybersecurity skills gap, while the global workforce gap has reached 4.8 million unfilled roles.
The outcome is predictable. Analysts learn speed instead of judgment. Confidence grows slowly. After months of repetitive work, many leave for roles that promise deeper investigations and more meaningful impact. On average, an analyst tenure lasts one to three years.
Then the SOC posts the job again.
.jpg)
Redefining the Analyst Role Before You Hire Again
The solution is to change what you are hiring analysts for.
Let autonomous AI do the heavy lifting. Think of it as the Level 1 analyst you wish you could afford to hire 50 copies of.
Here is how it works:
.jpeg)
Alerts generated by existing security tools such as EDR, SIEM, email security, identity, and network controls are sent to the Qevlar API. Qevlar consumes the alerts and uses them as the starting point for investigation.
Once an alert enters Qevlar, its Graph AI Orchestrator automatically runs a full investigation across multiple domains. It pulls logs and telemetry from endpoint, identity, network, email, and SIEM systems, enriches them with external threat intelligence, and adds business and historical context specific to the environment.
Qevlar correlates all of this data, validates signals across multiple layers, and determines whether the alert represents real risk or noise. This process covers triage, investigation, and recommended remediation steps without human intervention.
The output is a structured investigation report with context, evidence, confidence scoring, and clear next actions.
That report is delivered to analysts through the Qevlar UI or pushed directly into existing SOAR and ticketing systems such as ServiceNow, Tines, or Jira.
This changes the role immediately.
New hires investigate fewer cases, yet each case is richer and more educational.
Senior analysts spend time improving detections, handling complex incidents, and strengthening defenses.
Almond, a large managed security service provider, faced the same pressure as many SOCs. Alert volume increased steadily, and adding analysts wasn’t a sustainable option.
They integrated Qevlar AI into their orchestration stack. When alerts trigger, the AI autonomously investigates them and produces structured outputs that enable analysts to take informed decisions faster.
Thanks to Qevlar, Almond automated more than 80% of alert handling and reduced mean time to remediation to under 5 minutes without adding new analysts.
The integration of Qevlar AI is part of the ongoing optimization of the Almond CWATCH SOC. For several years, Almond has been building a robust technology ecosystem, combining cutting-edge SOAR, SIEM, and XDR solutions with its own platform: ITERA, for advanced, managed-as-code detection, and M&NTIS, for attack simulation and cyber defense optimization.
Julien Steunou, Managing Partner Security Services, Almond (read the full story)
Conclusion
Hiring another analyst is often necessary because many SOCs genuinely need the help. But the more important question is what that analyst will spend their time doing.
On day 1, are they being handed thousands of raw alerts to work through, or a prioritized view that points to real threats and real decisions? Do they have the tools that allow them to pull all the needed context without gathering it across hundreds of sprawled tools?
The job description sets expectations, but it’s the workflow that determines whether those expectations are met.
When AI handles the heavy lifting, such as repetitive alerts, hiring starts to reduce pressure instead of resetting the cycle. Analysts stay longer, learn faster, and deliver the work they were hired to do.
That is how SOCs break the loop they all recognize too well.






