How Qevlar AI Prevented the TamperedChef Attack

TL;DR:
- A sophisticated cybercrime campaign used Google Ads to distribute a trojanized PDF editor that, after 56 days, transformed into credential-stealing malware.
- An EDR solution flagged a low-severity Suspicious Process Discovery alert. Qevlar AI autonomously investigated this weak signal in just 4 minutes and exposed an active attack that had already begun credential exfiltration, identifying malicious process chains, stolen credentials, and command-and-control traffic before the attacker could move laterally or escalate access.
- The threat was contained before the stolen credentials could be operationalized, preventing a likely breach.
The Wolf in Sheep's Clothing
It started like any other afternoon. An employee downloaded what appeared to be a legitimate PDF editor after clicking a Google Ad. The software even displayed a proper EULA, complete with digital certificates from seemingly legitimate Malaysian companies. Everything looked normal.
But beneath the surface, something far more dangerous was unfolding.
The application, marketed as "AppSuite PDF Editor," had been part of a carefully orchestrated 56-day campaign.
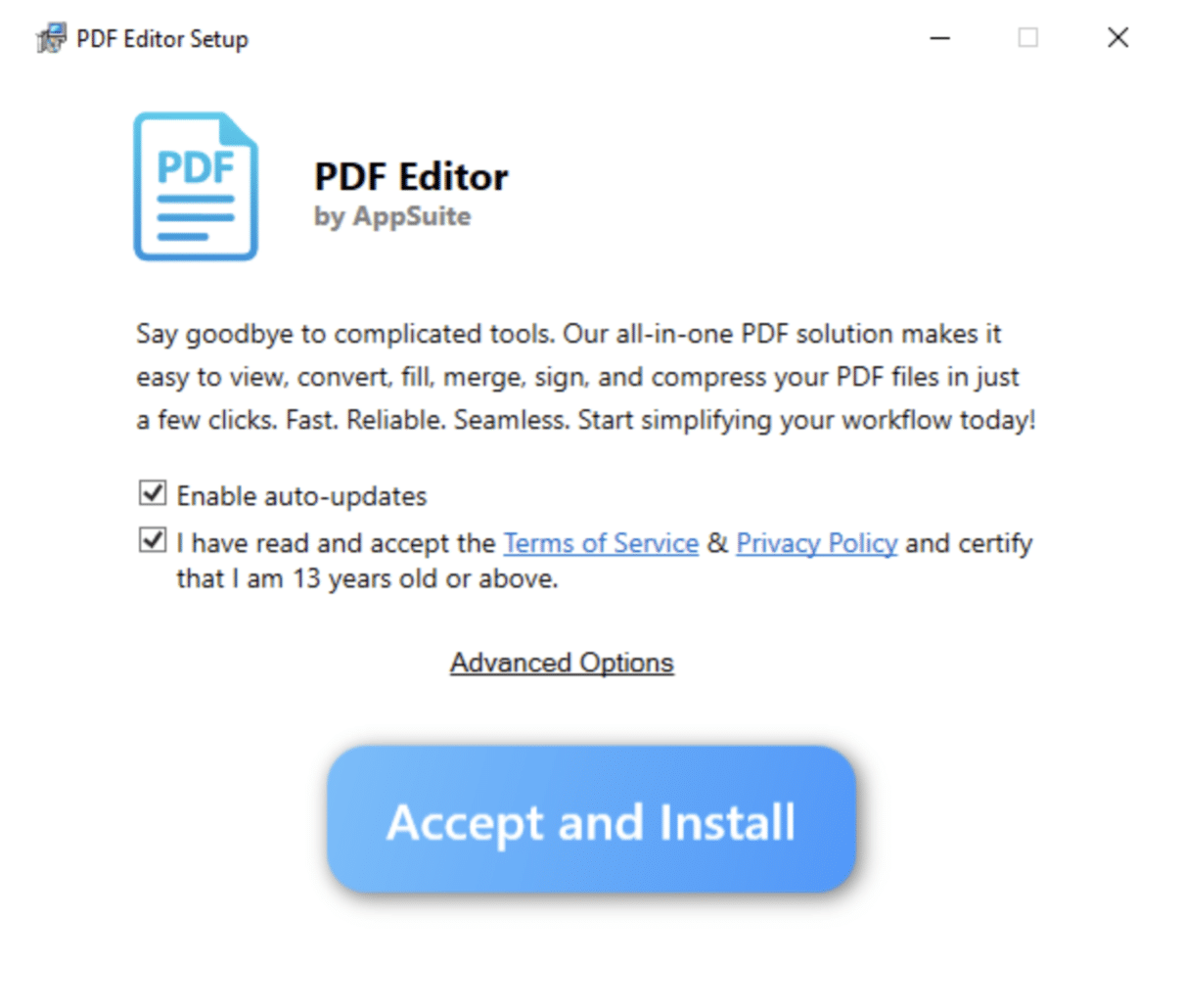
For nearly two months, it behaved exactly as advertised: a simple, functional PDF tool. Then, on August 21, 2025, machines that had installed the software received a silent update. Overnight, thousands of installations were transformed from utility software into TamperedChef, a sophisticated information-stealing tool.
How Did AppSuite PDF Editor Execute the Attack?
What made this attack particularly dangerous was its execution strategy. The attackers didn't just create malware; they engineered trust over time.
The campaign leveraged multiple fraudulent websites, all promoted through Google Ads with at least five different campaign IDs. The 56-day delay before weaponization aligned perfectly with typical Google advertising campaign lengths, suggesting the attackers deliberately waited for maximum distribution before activating malicious capabilities.
The software came signed with certificates from multiple Malaysian companies registered at the same address, each claiming to specialize in "digital transformation." These weren't stolen certificates; they appeared to be purpose-built shells designed to pass verification checks. Even the company websites looked legitimate, though likely AI-generated.
.png)
Once activated, TamperedChef moved with surgical precision. It queried system defenses, terminated browser processes to access locked credential stores, and established HTTPS connections to command-and-control servers. The malware specifically targeted Chrome and Edge Web Data files, seeking the keys to corporate accounts, email systems, and SaaS applications.
But It’s the Story With the Happy End
This is where the story diverges from the headlines you typically read about ransomware incidents and data breaches.
All Qevlar AI’s customers managed to identify the threat before it caused any damage thanks to the fact that Qevlar investigates 100% of alerts (even the lowest severity ones), leaving no room for attackers to slip through.
At 16:00, the malicious process chain was detected. PDF Editor.exe spawned PowerShell and taskkill.exe, classic signs of arbitrary command execution and security process termination. Most concerning was the access to browser credential stores.
By the time Qevlar began its investigation, a subset of credentials had already been exfiltrated to attacker-controlled infrastructure.
By 16:04, Qevlar AI had completed its investigation. The full attack path was mapped, the scope was determined, and containment recommendations were delivered. Analysts were able to immediately revoke exposed credentials, isolate the endpoint, and block command-and-control infrastructure before the attacker could reuse the stolen access.
What Did Qevlar AI Prevent?
Although credentials were exfiltrated, the attack was stopped before those credentials could be leveraged. There was no evidence of lateral movement, no privilege escalation, and no secondary payload delivery. The command-and-control channel was identified and neutralized before it could be used for follow-on activity.
Consider what could have happened without rapid detection:
Credential Abuse at Scale: Stolen browser credentials often include VPN access, email accounts, cloud services, and administrative portals. Without a rapid response, attackers could have authenticated directly into core systems.
Lateral Movement: With valid credentials, attackers typically spend 200+ days moving quietly through environments, escalating privileges and expanding access.
Data Exfiltration: What began as limited credential theft could have expanded into sustained data exfiltration of intellectual property, financial data, or customer records.
Ransomware Deployment: Information stealers frequently act as the first stage in ransomware campaigns. Delayed detection often results in full-environment encryption weeks later.
A four-minute investigation window versus four days or four weeks is the difference between credential rotation and business shutdown.
Conclusion
A low-severity Suspicious Process Discovery alert is exactly the kind of signal that gets buried under thousands of daily notifications. It's easy to dismiss, easy to deprioritize, and easy to miss entirely when analysts are drowning in false positives.
The attacker was already inside. The malware was already active. What mattered was whether anyone would investigate that single low-priority alert among the noise.
Do you want to check that there isn’t a wolf in sheep's clothing in your environment?
Put Qevlar AI to the test: connect it via APIs to your alert sources and assess the results in hours. Get started here: https://www.qevlar.com/






